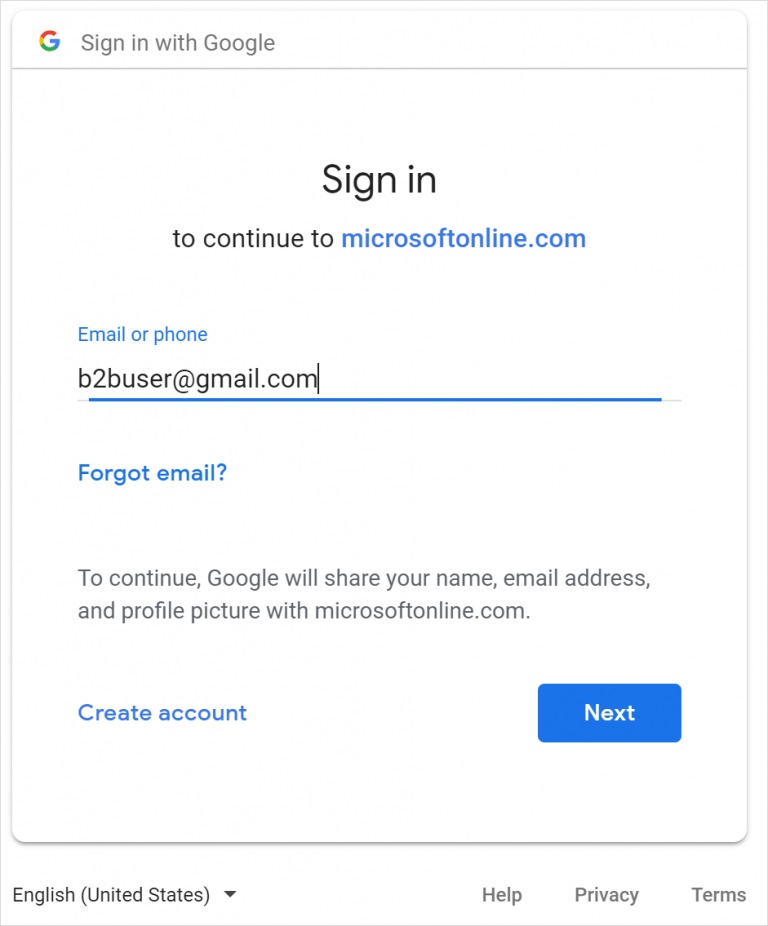
In an announcement on its Azure blog, Microsoft confirmed Azure Active Directory B2B now allows organizations to use other IDs, namely Google accounts. This is a substantial change as the company previously locked users to a Microsoft Account or Azure AD account. What’s interesting about this is Microsoft is not being crafty and making the Google sign-in process complicated. In fact, just a single sign-on process is in place. It is worth noting that the ability is currently in preview and additional back-end management will need to be conducted before implementing. Namely IT admins will need to create two phases, a first is a Google developer project that allows the OAuth client ID API to be used. Secondly, the Google allowance for sign-in will have to be set up in Azure Active Directory.
While Google sign-in is now excepted, access is not exclusive to the company. Microsoft points out Google is simply the first on board and wider support for non-Microsoft accounts is incoming. “We are working to add support for other standards-based identity services, but we have no additional partnership to announce at this point,” a Microsoft spokesperson explained. Azure Active Directory Business to Business has been available since last year. It is an extension of the Active Directory platform,
Windows 10 Logon
Earlier today, we reported on a Google Chromium project to bring Gmail as a credential provider to Windows 10. This means an email address linked to Google (Gmail) to login to Windows 10. Google will be coming on board with authentication through its Google Accounts and ID Administration (GAIA). The credential provider features an installer executable called gcp_installer.exe and will feature the gcp_setup.exe, startchromeonfirstlogin.cmd, gaia1_0.dll, and gcp_eventlog_provider.dll files.